Web-Based Supply Chain Attacks in the Enterprise
July 4th, 2019 | By Jscrambler | 3 min read

A web-based supply chain attack can breach your enterprise via third-party vendors. Hence, a company's website or web app has become the perfect stage to steal its users' data.
Data breaches were perceived as a direct result of attackers gaining unauthorized access to a database. Companies were urged to protect everything inside the firewall. Arguably, the servers of today's enterprise are more secure than ever, as new legislation like GDPR has pushed forward hefty fines for data breaches.
Despite this push for increased security, some reports found a 424% increase in data breaches in 2018. Other research pointed out that 59% of companies experienced a data breach caused by one of their vendors or third-parties.
First-party data breach vs. Third-party data breach
Here we find two distinct approaches by which companies can be breached. While a first-party data breach most often requires attackers to infiltrate a database, third-party data breaches originate from attackers going after the enterprise's smaller, less secure providers, which are the weakest link in the supply chain; hence the term supply chain attack.
Zooming into 2018 and 2019, we find a clear pattern in supply chain attacks targeting the enterprise: a web-based vector of attack.
Attacks on Equifax, British Airways, Ticketmaster, and Forbes were achieved with malicious code that was injected into the companies' websites and then run in their users' browsers. A company's website or web app has become the perfect stage to steal its users' data.
Most third-party code providers don’t have enterprise-grade security systems, and yet this external code has the same permissions as the code that companies develop in-house. — Pedro Fortuna, Jscrambler's CTO, on TechRadar.
Web-based Supply Chain Attacks thrive because it's not hard for attackers to find a poorly secured third-party used by one or several large enterprises.
Let's not forget that 67% of the scripts loaded in today's average web app come from third-parties.
When we move past scripts from reputable sources like Google, we find others that are built and maintained by a single developer. Such was the case of the event-stream incident, where all it took was for the malicious actor to ask the original developer for access to maintain the code base.
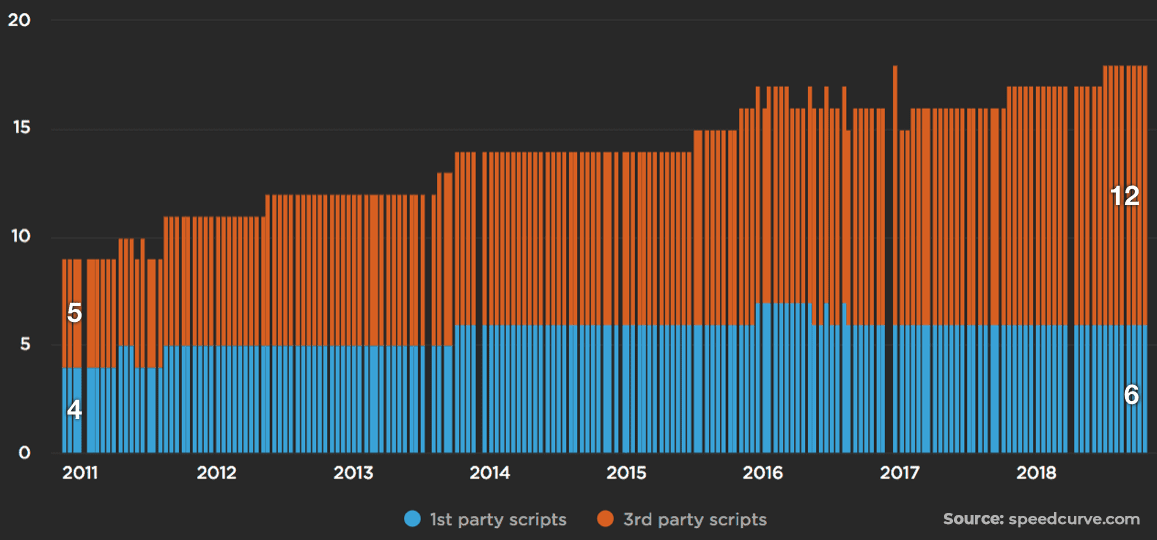 When the attacker compromises these third-party scripts by injecting malicious code, companies' perimeter defenses fail to detect the attack since it was initiated in a component of the system that was trusted by default.
When the attacker compromises these third-party scripts by injecting malicious code, companies' perimeter defenses fail to detect the attack since it was initiated in a component of the system that was trusted by default.
How do you mitigate web-based supply chain attacks?
Whether the attack seeks to steal user credentials, use the user's computer to mine cryptocurrency, or steal the user's credit card (such is the case of Magecart attacks, which amounted to over 50,000 incidents in 2018), the fact remains that current approaches fall short. Short enough to put entire businesses at stake.
Much like today, it is inconceivable for an enterprise not to have a Web Application Firewall (WAF) in place, there's too much on the line not to have a client-side security system that actively detects and mitigates web-based supply chain attacks in real-time.
If you're interested in learning more about these attacks and seeing a demonstration of Webpage Integrity's mitigation approach, book a demo!
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
How Your Code Dependencies Expose You To Web Supply Chain Attacks
In this blog post, we’ll walk you through the risks of code dependencies when it comes to web supply chain attacks.
August 13, 2021 | By Pedro Fortuna | 4 min read
Is the Enterprise on the Brink of a Global Web Supply Chain Attack?
A recent study put the npm ecosystem under the microscope to find key security threats. Here, we dissect these findings and their meaning to the enterprise.
November 12, 2019 | By Pedro Fortuna | 4 min read
