Magecart Attacks in eCommerce: Road to Mitigation
July 15th, 2021 | By Jscrambler | 4 min read

Dive into the strategies of companies like Amazon, Etsy, Mercado Livre, and ASOS to protect their users against Magecart attacks in eCommerce.
The COVID-19 pandemic has propelled eCommerce forward and increased the number of people buying online.
The cyber attackers are taking advantage of the increased eCommerce sales and preying on major companies since more users shopping online directly translates to a bigger potential payoff for attackers that target sensitive user data.
How can eCommerce companies fight off attackers and protect their websites?
Understand how eCommerce companies can mitigate Magecart web skimming attacks and protect their users.
What are Magecart Attacks?
Magecart is a collective of cybercriminal groups that inject digital credit card skimmers on eCommerce and payment websites. These groups have been active since 2015 but have gained momentum from 2018 onward.
In a Magecart attack, attackers inject the skimmer (through malicious JavaScript code) into a company’s payment page.
This code collects credit card details whenever a user submits them in a form (formjacking) and sends them to attacker-controlled drop servers. During this process, neither the end-user nor the company had any awareness that the attack had taken place.
Attackers may gain access to the victim’s website in two typical ways:
First-party attack
The skimmer directly places the malicious code on the payment page in a first-party attack, having access to the targeted website.
Third-party attack
Third-party attack: Injecting the malicious code through a third-party provider that the victim company is using (such as a live chat tool, analytics service, or code dependency).
Third-party Magecart attacks
Third-party Magecart attacks are critical because they don’t require a first-party server breach or direct access to the company’s website.
They target weaker third parties, which often have fewer resources dedicated to security. And because that (infected) third-party code has all the same permissions as all the other code on a website, it can readily tamper with any payment forms, collect all submitted data, and send it to the attackers’ servers without ever being detected by Web Application Firewalls.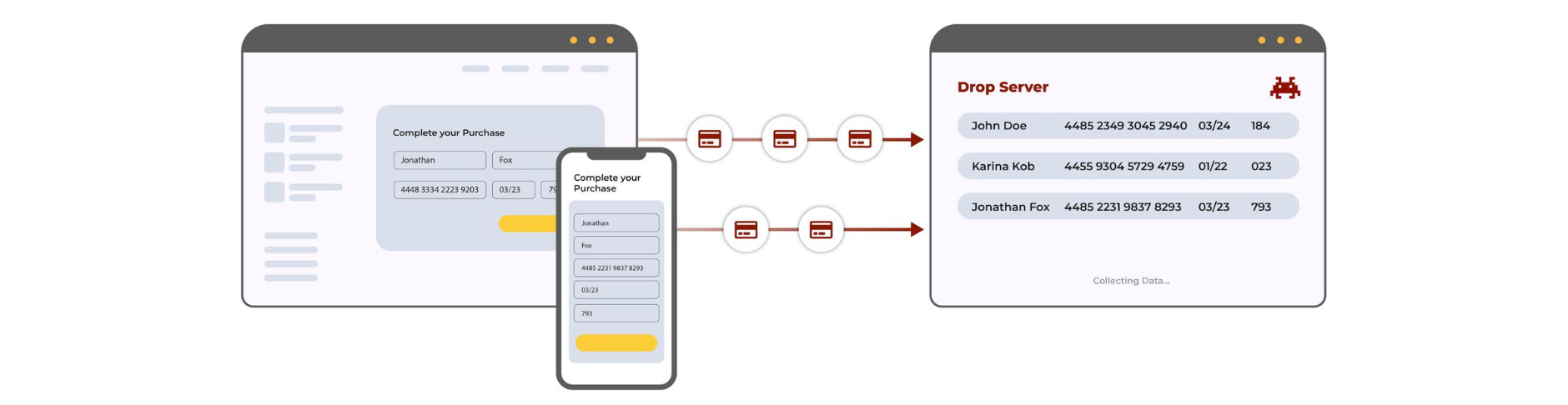
The bottom line is that thanks to this client-side security blindspot companies have, attackers can orchestrate attacks that are scalable and that require lower effort when compared to directly breaching a major company’s first-party server.
Road to Mitigation: Visibility and Control
When we talk about mitigating Magecart web skimming attacks, there are two main points we need to consider: visibility and control.
Given that Magecart web skimmers often begin their attack by infecting third-party providers instead of their actual target website, we can see why eCommerce companies need complete visibility over their web supply chain.
Visibility is one of the first steps companies should take to limit the risk of Magecart attacks ever taking place.
Control comes after visibility, or mitigating possible attacks that may arise by blocking the infected website resource and blocking the leakage of credit card data to attackers’ servers.
Only by combining these two processes will companies achieve a security-in-depth approach on the client side.
How can companies choose a security solution that provides the needed visibility and control?
How to assess a security product
Step 1: Complete website inventory
An adequate Magecart mitigation solution should provide companies with a complete website inventory.
This will ensure they have visibility into the scripts and network connections that take place in any given user session, while also making it easier to learn which behaviors are normal and which ones are malicious. It is crucial to fight off the client-side security blind spot associated with third-party code.
Step 2: Real-time visibility
After the website inventory overview, it’s critical to have real-time visibility of how each individual script is behaving on their website.
This visibility allows companies to detect suspicious behaviors, such as a known script suddenly starting to tamper with a payment form (Magecart web skimming attack) or attempting to send data out to an unknown domain (data leakage). Considering that Magecart web skimming attacks remain active for 22 days on average before being detected, this real-time visibility can improve incident response and contain possible data leaks.
Step 3: Control
Because visibility is half of the response needed for a security-in-depth approach, companies need complete control over the behavior of each script.
Effective control means being able to restrict specific allowed or disallowed behaviors in real-time so that any attempt at malicious activity (e.g., leaking user data, showing a popup on top of the website) is blocked, stopping the attack from happening.
To achieve this level of control, companies need to look for solutions that allow a flexible rule-based approach that blocks all malicious activity on the client side.
Approaches based on a Content Security Policy (CSP) are limited since they lack this level of granularity and can be easily bypassed.
Since Magento mitigation is a complex topic and mainstream security solutions aren’t capable of preventing these attacks, it’s important that eCommerce companies know how to assess a security product based on technical requirements.
To do that, they must perform tests to ensure that the solution meets those requirements. For an in-depth explanation of what tests are needed, check out our Magecart mitigation checklist.
Conclusion
Although Magecart mitigation is a complex issue, companies can fight it off by fixing their client-side security blindspot with adequate security solutions.
The sooner they start addressing the security weaknesses of their web supply chain, the better they will be able to protect their users in the long run and ensure compliance with data protection regulations such as GDPR and CCPA and standards such as PCI DSS.
By adopting a solution that is behavior-based and that runs in real-time, companies will gain the required visibility and control over the behavior of their website’s scripts. That allows us to mitigate the attackers targeting the eCommerce industry and prevent critical attacks such as Magecart web skimming.
Jscrambler is offering a free website inventory report. This report has helped major airlines and retailers uncover key client-side security threats and minimize their exposure to web supply chain attacks.
Embrace this chance to gain increased client-side visibility!
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
3 Main Steps to Prevent Magecart Attacks
Magecart credit card skimmers are breaching more and more companies. Here are 3 main steps to ensure your business can properly prevent Magecart attacks.
March 31, 2020 | By Pedro Fortuna | 5 min read
How To Protect Your Organization From Magecart
2020 has been ripe with high-profile Magecart attacks that have breached major organizations. Learn about the best magecart prevention tactics.
August 4, 2020 | By Pedro Fortuna | 5 min read
