[Case Study] Mitigating Browser Extension Attacks
April 5th, 2019 | By Jscrambler | 7 min read
![[Case Study] Mitigating Browser Extension Attacks width=](/img/containers/images/jscrambler-blog-case-study-mitigating-browser-extension-attacks.jpg/00fafa06621a1de0adc3c299846fc561.webp)
Real-time webpage monitoring helps mitigate browser extension attacks. The Jscrambler Research team developed this case study.
For many of us, browser extensions have become part of being online. 50% of the billion Google Chrome users use extensions to customize their browsing experience.
Most often free, extensions enable us to get extra features directly from the browser. Several software companies have created browser extensions to deliver their products, as they provide a seamless user experience.
But then there is the other side of the coin: when extensions are used as an attack vector to exploit their end-users.
Browser Extensions: the Danger
Browser extensions pose a particularly dangerous attack vector, as they can execute in the background and a separate execution environment, inject malicious JavaScript directly into webpages and modify the DOM.
When installing a browser extension, end-users must consent to a set of requested permissions. More often than not, this is the scenario: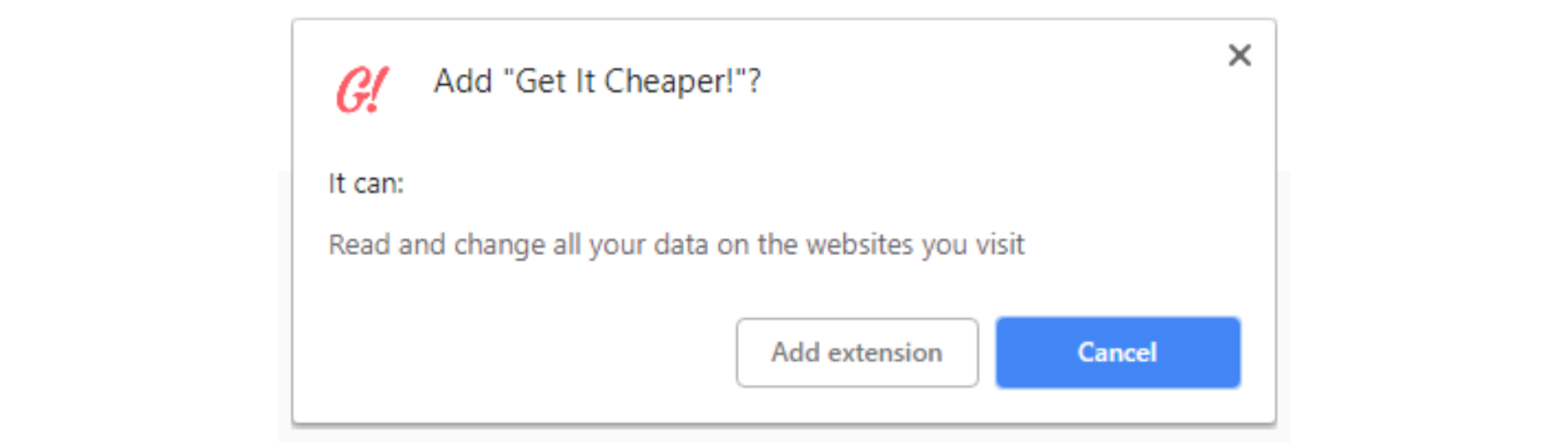 To use such an extension, users must grant it full privileges to read and modify all data on the visited websites. In the typical case of a legitimate and harmless extension, this allows it to change the DOM and place a popup over a website, for example.
To use such an extension, users must grant it full privileges to read and modify all data on the visited websites. In the typical case of a legitimate and harmless extension, this allows it to change the DOM and place a popup over a website, for example.
However, this also means that a malicious browser extension can abuse these permissions to trick and harm the end-user, namely by displaying a phishing popup over a bank's website, or by monitoring an e-commerce checkout page, capturing all credit card information, and sending it to attackers' servers. All without users' knowledge.
A well-known attack via a browser extension occurred when the MEGA.NZ Chrome extension came under the control of hackers and started leaking the usernames, passwords, and cryptocurrency private keys of its 1.7 million users to a hacker-controlled server. The attack spanned for four hours before the extension was updated to a clean version.
However, this approach of compromising a legitimate extension is not the only way to infect end-users. Thousands of malicious extensions have been submitted to the Chrome Web Store, according to Google’s figures, over the last few years, 1 out of 10 submitted Chrome extensions were malware, despite their efforts to filter them.
All of this has motivated the Jscrambler Research team to evaluate how malicious we can get with a browser extension, by creating a Man-in-the-Browser proof of concept.
Our Man-in-the-Browser Extension
The extension created to be used during the PoC was named "ZeroAds", a seemingly legitimate ad-blocking extension among many others currently available. This was not chosen at random but to be useful and stealthy (seemingly inoffensive), something that a malicious agent would do.
The ZeroAds extension contains a fair portion of legitimate code to remove ads, within which resides some advanced Man-in-the-Browser (MitB) features, such as header tampering, redirects, remote code execution, tamperings (web injects), form grabbing, etc. We will go over how these features performed on a sample attack scenario further on.
Publishing and Spreading the Extension
The extension was submitted for approval to the Chrome Web Store. As it so happens, it successfully passed Google's screening and became publicly available for download.
Several tactics were used to avoid detection, including choosing an unsuspecting title and icon, requesting minimum permissions, and encrypting payloads.
Note: this extension wasn't able to place any harm on any end-user who could have downloaded it during the time it was available; it got no external downloads.
This shows us that attackers can publish a malicious extension by passing it as a seemingly legitimate one. Then, it's a matter of getting users to install it.
There are two approaches: either through publicity by convincing users to install them voluntarily, or without their consent or knowledge, possibly by sending phishing emails with malicious macros, drive-by download websites, or pull requests to open-source extensions on GitHub.
It should also be noted that the Chrome Web Store may have since put in place improved detection mechanisms to better filter out malicious extensions.
Extension Capabilities and Attack Scenarios
Header Tampering: Bypassing CSP
Unlike most attack vectors, browser extensions have the particularity that they can completely remove all HTTP headers. This is especially important because most client-side security standards, such as Content Security Policy (CSP), rely on HTTP headers.
By stripping the CSP header, therefore bypassing it, attackers can enable the site to receive and send data to unauthorized websites — such as sending captured user credentials to hacker-controlled servers or serving a malicious credit card skimming script from an external source.
To achieve this, our extension contains a header tampering script, which uses Chrome's WebRequest API:
"*://content-security-policy.com/*": {
"headers": {
"response": {
"Content-Security-Policy": ["capture", "drop"],
"X-Content-Security-Policy": ["capture", "drop"],
"X-WebKit-CSP": ["capture", "drop"]
}
}
}
The code snippet above is a portion of our extension's config file which enables it to remove CSP on an example website (content-security-policy.com), which quickly allows us to test if a CSP is present or not. If a CSP is active, it should show a green "CSP Supported" message and block an image from loading on this page: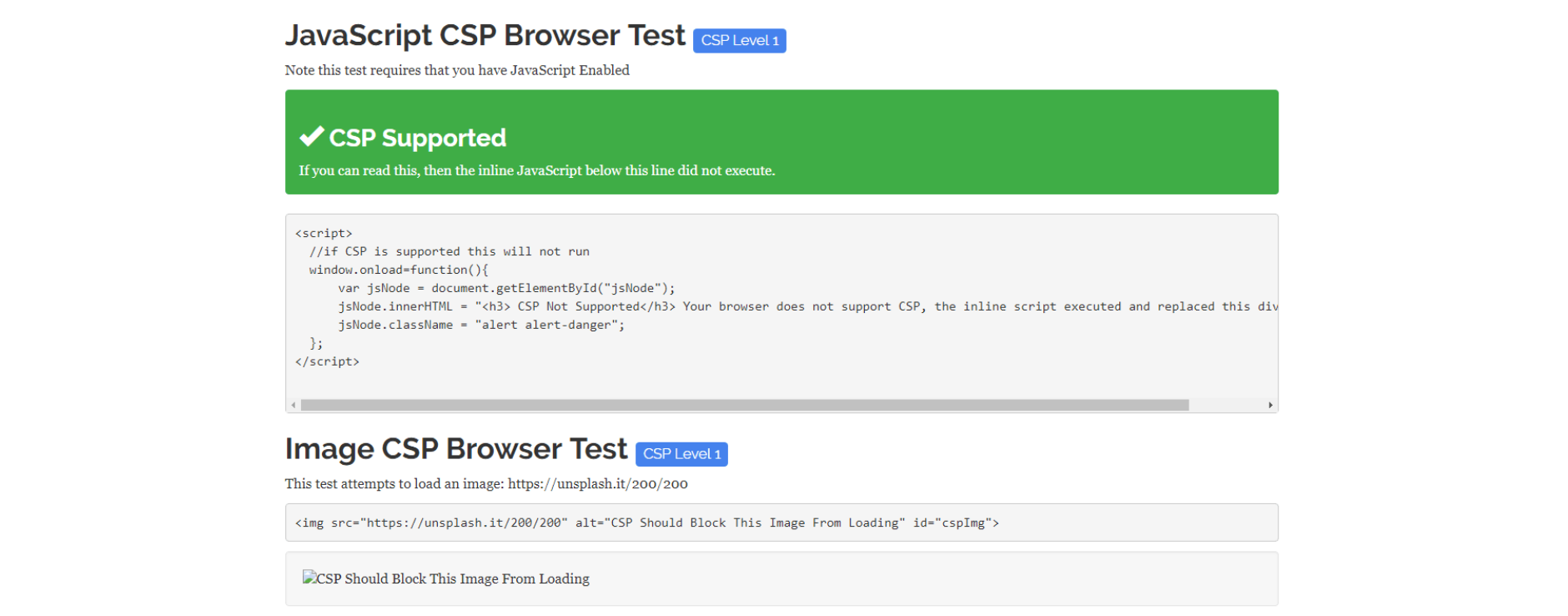
When we reload this web page with the malicious ZeroAds extension enabled, we can immediately see that the CSP was successfully removed and the image is no longer blocked: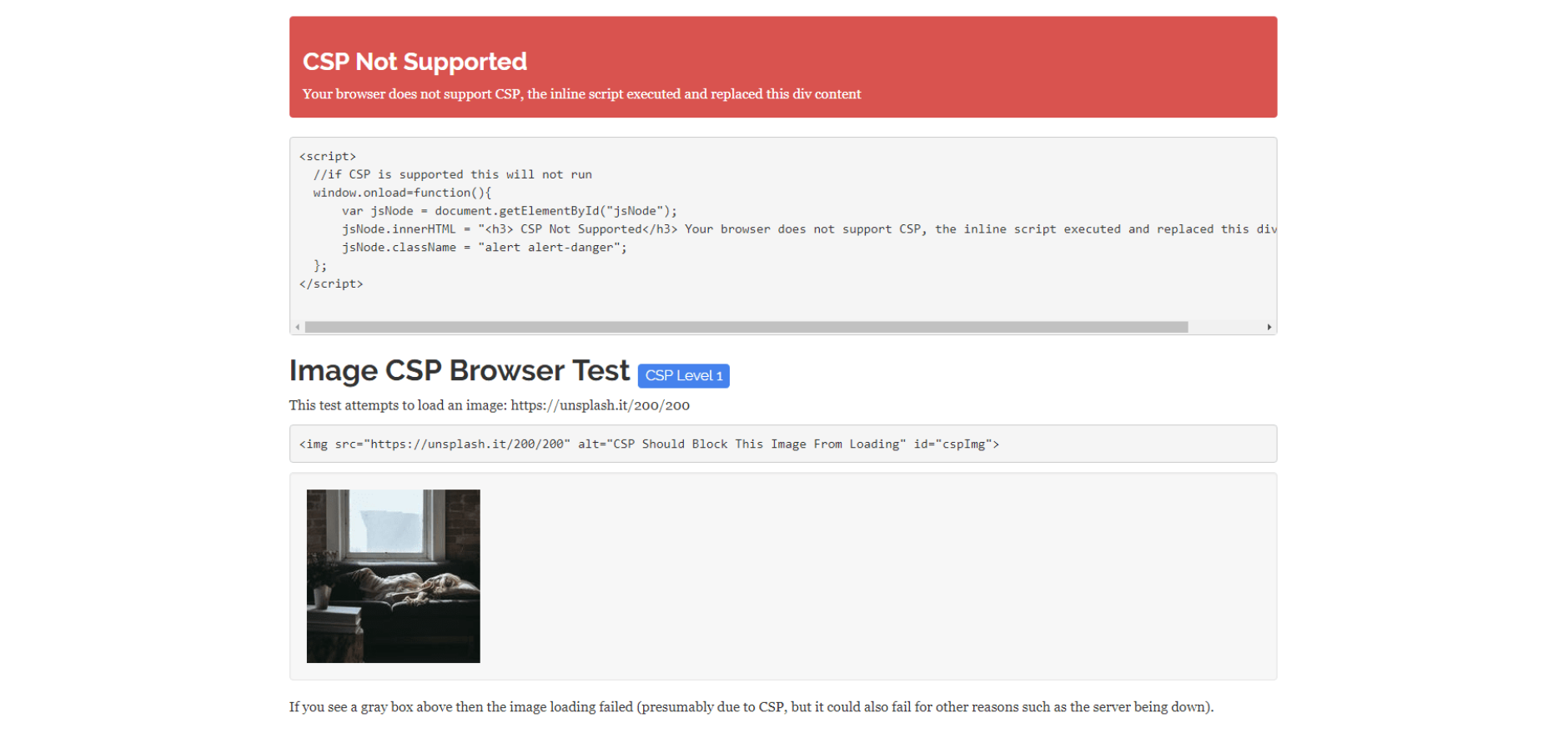
Stealing User Data
Apart from successfully removing headers, the extension is also able to perform other types of attacks. One such example is form grabbing:
”<URL>": {
”grabber": [<FORM FIELDS DO COLLECT>]
},
This form grabber can fetch data from POST messages and XHR messages. As so, it can be used to steal user credentials on a login page, skim credit card data, or leak Personally Identifiable Information (PII).
Testing this with our ZeroAds extension enabled on a login page, we got the form grabber's results in a JSON file which contains the captured email and password:
{
"name": "grabber",
"data": {
"email": "[email protected]",
"locale": "en_GB",
"login_source": "login_location",
"pass": "capturedPassword",
"timezone": "240"
}
}DOM Tampering
With just a few lines of code, a malicious browser extension can tamper with the Document Object Model (DOM) to trick users, steal or tamper with data, and perform redirects.
Using the configuration shown below, the malicious browser extension can modify the DOM by injecting JavaScript code into the webpage using dynamic content scripts:
”<URL>": {
”execute": “<JAVASCRIPT CODE>”
},
To test this capability in a plausible attack scenario, we configured the extension to:
modify the DOM when infected users visit a legitimate banking website legitimate-bank.com;
display a popup that links to malicious (but seemingly legitimate) mobile applications, as shown below.
"*://legitimate-bank.com/": {
"execute": "if (window.location.toString() !== 'http://virtual-bank.jscrambler.com/') { return; } var overlay = document.createElement('div'); overlay.setAttribute('id', 'overlay'); overlay.setAttribute('class', 'ad-overlay'); /* (...) */ document.body.appendChild(overlay);"
}
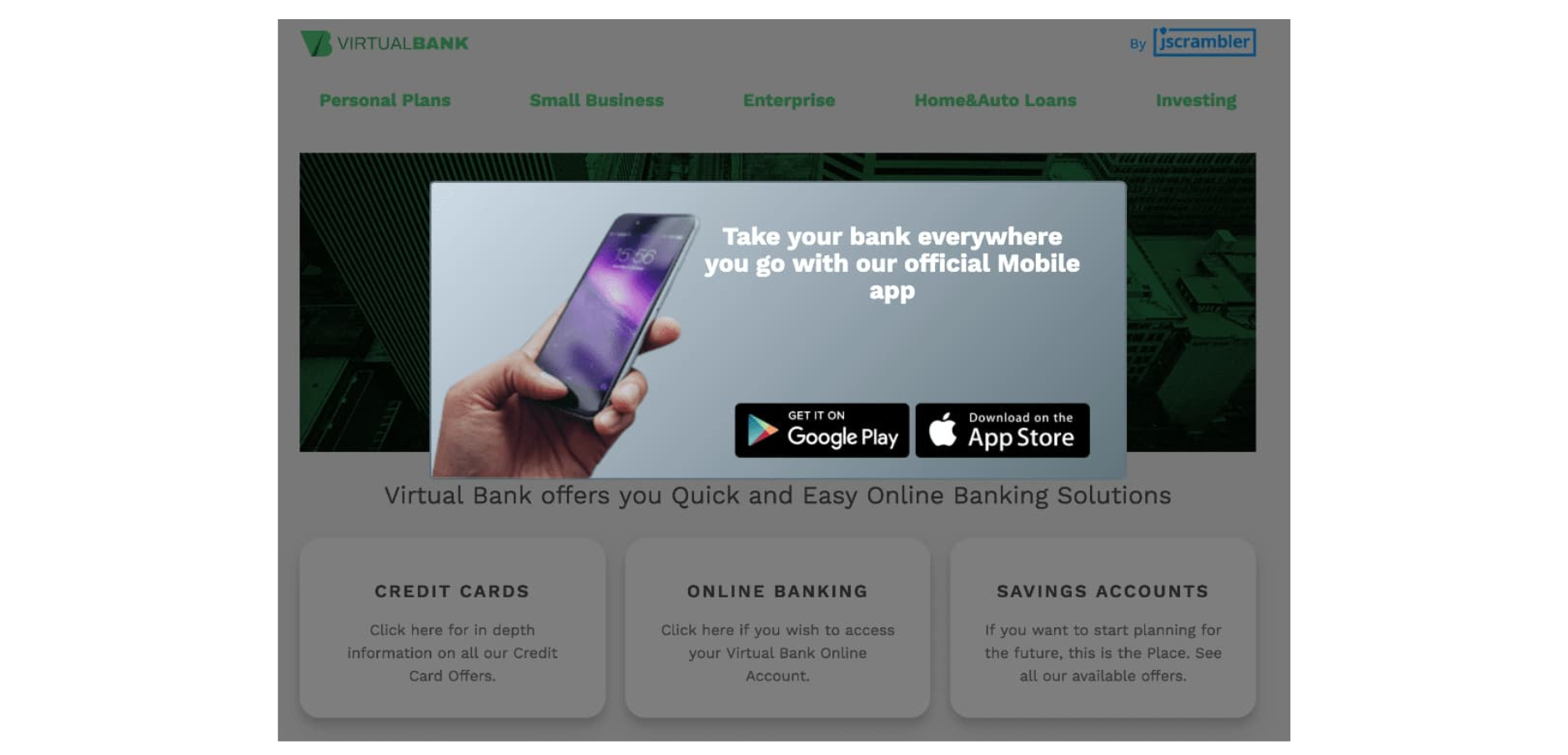
Because this is happening on a trustworthy website, it’s entirely likely that some users trust this information and install the malicious apps — which may mimic the bank’s mobile application and steal users’ credentials.
Mitigating the Attack
Common Approaches
Security solutions such as anti-virus and anti-malware are historically ineffective at detecting malicious JavaScript, as malicious logic can be concealed by attackers and even be changed over time to avoid detection.
Other approaches such as device fingerprinting, geo-location, and bot mitigation are useless in this case, as this is still a legitimate user using a legitimate device on his or her normal geolocation, which is identified as normal behavior, remaining completely undetected.
Jscrambler Real-time Webpage Monitoring
A different approach to mitigate browser extension attacks is through real-time webpage monitoring to verify the integrity of the webpage. This continuously monitors for DOM modifications/injections, tampering with native APIs, and tampering with events. It follows an allowlisting approach, so it's able to detect every client-side threat while tackling false positives.
With this system, a real-time notification is displayed on a dashboard whenever a client-side threat takes place. Simultaneously, this can trigger an immediate countermeasure from the application to mitigate the attack.
Framing this solution to the attacks shown before, when the extension performs any sort of code injection or tampering on the monitored webpages, the dashboard immediately displays a notification with precise information about the injected code and enables the application to break, remove the injected code, or perform another action.
This webpage's real-time monitoring solution has the added value of being simple (both in installation and usage), transparent, and not breaking the code.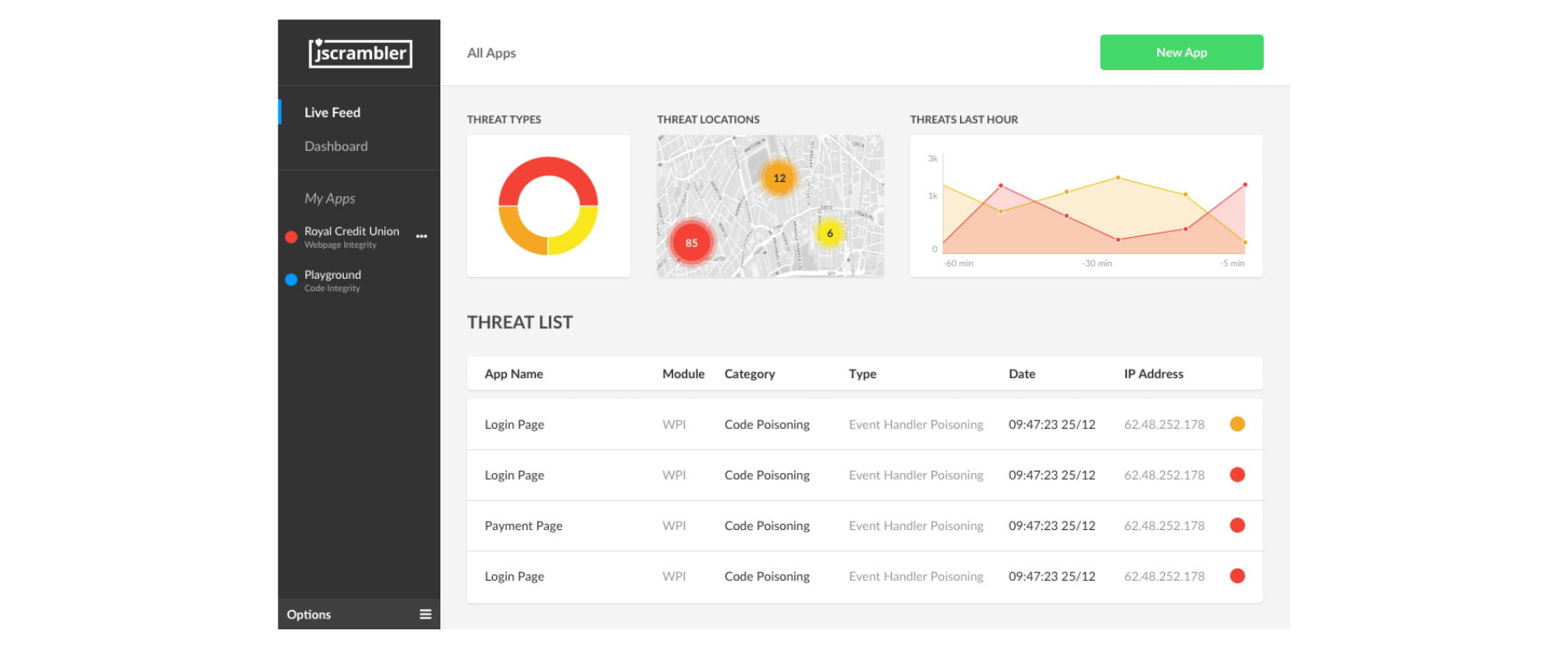
Closing Thoughts
As we were able to show during this PoC, current standards don't offer protection against Man-in-the-Browser trojans. Any header-based defense mechanism (including CSP) can be disabled.
As we see examples of this in the wild, it becomes clear that malicious agents are capable of creating, publishing, and distributing malicious extensions that infect thousands (or even millions) of users. Because they can tamper with the DOM, these malicious extensions enable attackers to exfiltrate sensitive information, trick users, and perform fraudulent actions (e.g. steal funds) — all this without any awareness from the end-user.
Solutions such as anti-virus, anti-malware, device fingerprinting, and bot detection aren't effective against these attacks. An effective approach is to gain complete visibility with a real-time webpage monitoring solution. This enables an immediate response, as the application itself can trigger a countermeasure to mitigate the attack.
If you're interested in learning how Jscrambler can protect your business, request a demo with our experts.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
How Secure is your Web Browser?
Pedro Fortuna points out that if companies continue to solely focus on protecting the server, they will leave their front door open to attacks.
January 20, 2017 | By Pedro Fortuna | 3 min read
The battle for payment card data is taking place in your browser
Shopping online is generally safe, but under the surface, there’s a war to keep our payment card data secure.
January 24, 2023 | By Jscrambler | 4 min read
