Auto-F(a)illing Password Managers
August 29th, 2023 | By Jscrambler | 6 min read

Password managers are a valuable tool for individuals and organizations to enhance their digital security.
By securely storing and auto-filling login credentials, password managers offer convenience and the ability to generate strong, unique passwords. However, it's vital to understand that password managers are not infallible.
This blog post dives into a potential security concern associated with auto-filling inputs and explores how users can mitigate the risks effectively.
The Danger of Automatic Auto-Filling
While password managers are designed to enhance security, their automatic auto-fill functionality can inadvertently introduce risks.
The primary danger lies in the possibility of a password manager automatically filling in credentials for untrusted or malicious websites. This scenario can occur when attackers manipulate website elements or create convincing phishing sites to deceive password managers.
If users unknowingly rely on automatic auto-fill without verifying the legitimacy of the page, their login credentials could be exposed to adversaries, potentially leading to account compromise.
Auto-Filling Sandboxed Iframes
In January, Google published an advisory informing users that "multiple password managers can be tricked into auto-filling credentials into untrusted pages". Hence, it could "lead to account compromise for any users using these password managers".
This was found to be happening on Safari browsers and in Bitwarden and DashLane extensions, where they would automatically auto-fill credentials in forms embedded into sandboxed iframes. By the time this advisory was published, these vulnerabilities had already been fixed.
What about Unsandboxed Iframes?
Our security research team performed tests on common browsers and password managers to determine how these would behave in the presence of same-origin and cross-origin iframes that were not sandboxed.
We created a test page that included four different scenarios when using iframes:
Same-Origin iframe without sandboxing;
Same-Origin iframe with sandboxing;
Cross-Origin iframe without sandboxing;
Cross-Origin iframe with sandboxing;
With these tests, we expect only the Same-Origin Iframes without sandboxing to be filled.
1. Firefox
We observed that the Firefox browser behaves as we expected. The autofill feature only fills the same-origin unsandboxed iframe and ignores all other cross-origin or sandboxed iframes.
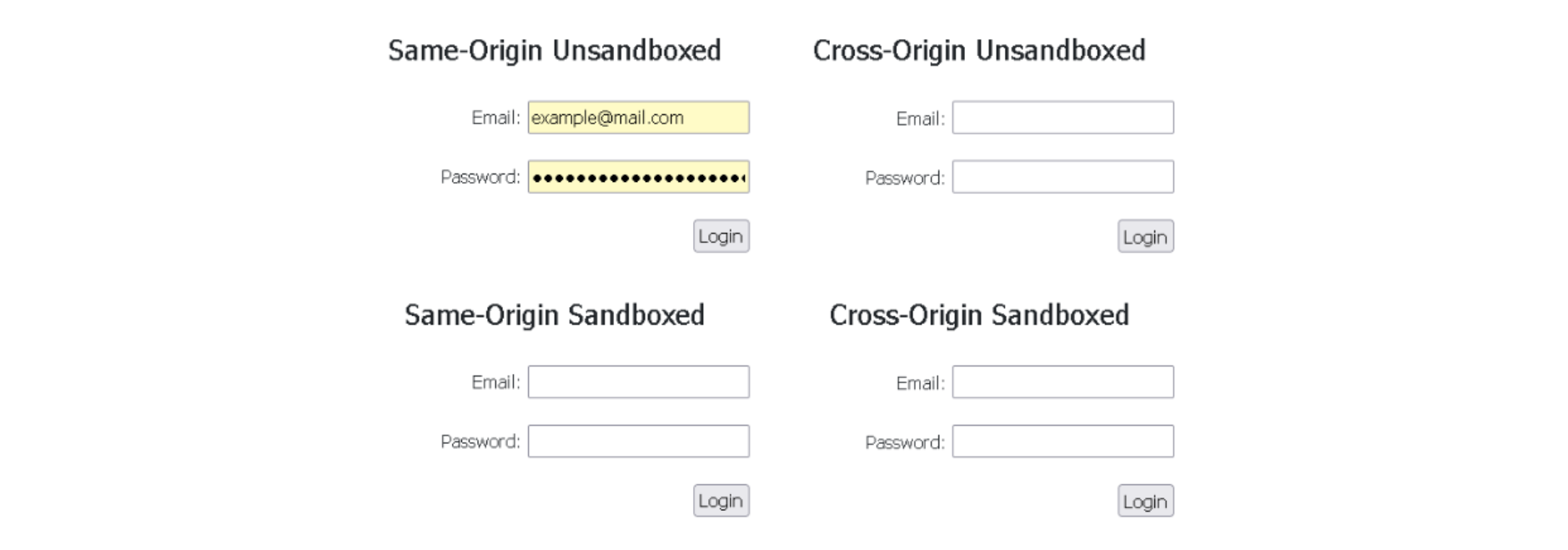 Image 1: Firefox browser only auto-fills the same-origin unsandboxed iframe
Image 1: Firefox browser only auto-fills the same-origin unsandboxed iframe
2. Chrome
Similarly to Firefox, the Chrome browser also displays the correct behavior. The autofill feature will only fill the same-origin unsandboxed iframe, ignoring all other cross-origin or sandboxed iframes.
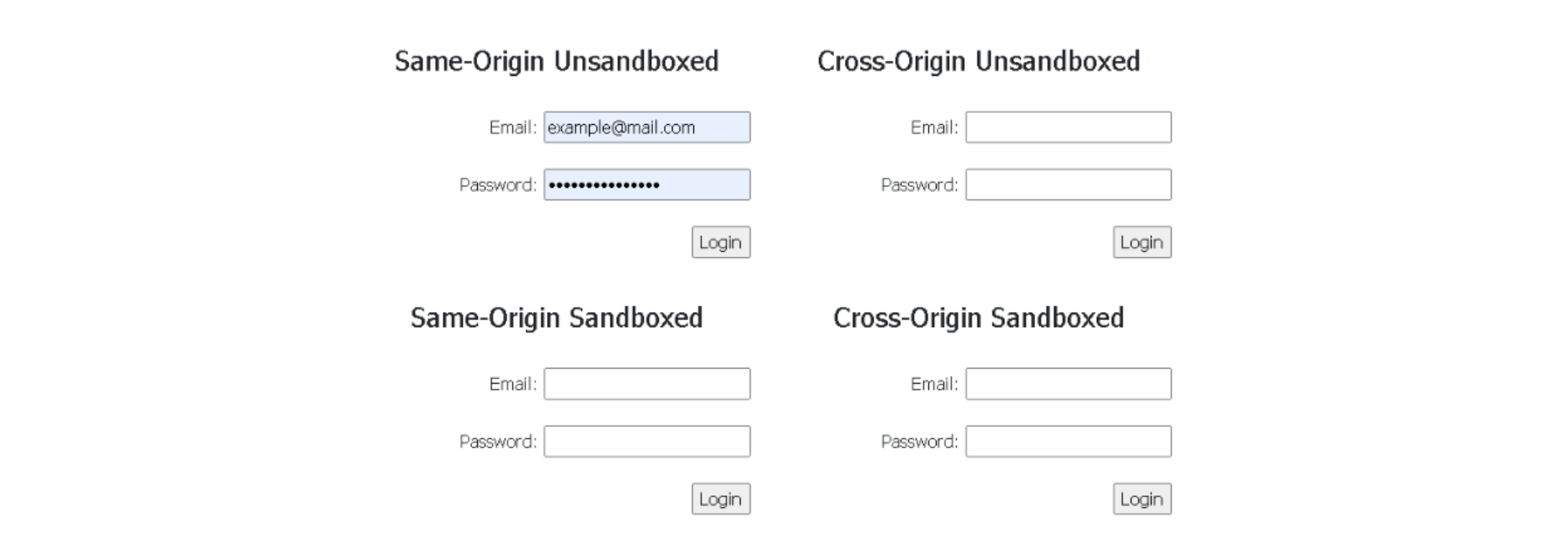 Image 2: Chrome browser only auto-fills the same-origin unsandboxed iframe
Image 2: Chrome browser only auto-fills the same-origin unsandboxed iframe
3. Edge
The Edge browser was found to display a slightly different behavior.
Even though it will still only autofill the password field on the same-origin unsandboxed iframe, as we expected, it will also autofill the username or email field in cross–origin or sandboxed iframes without warning the user that information will be sent to an external domain, which can be considered a security issue.
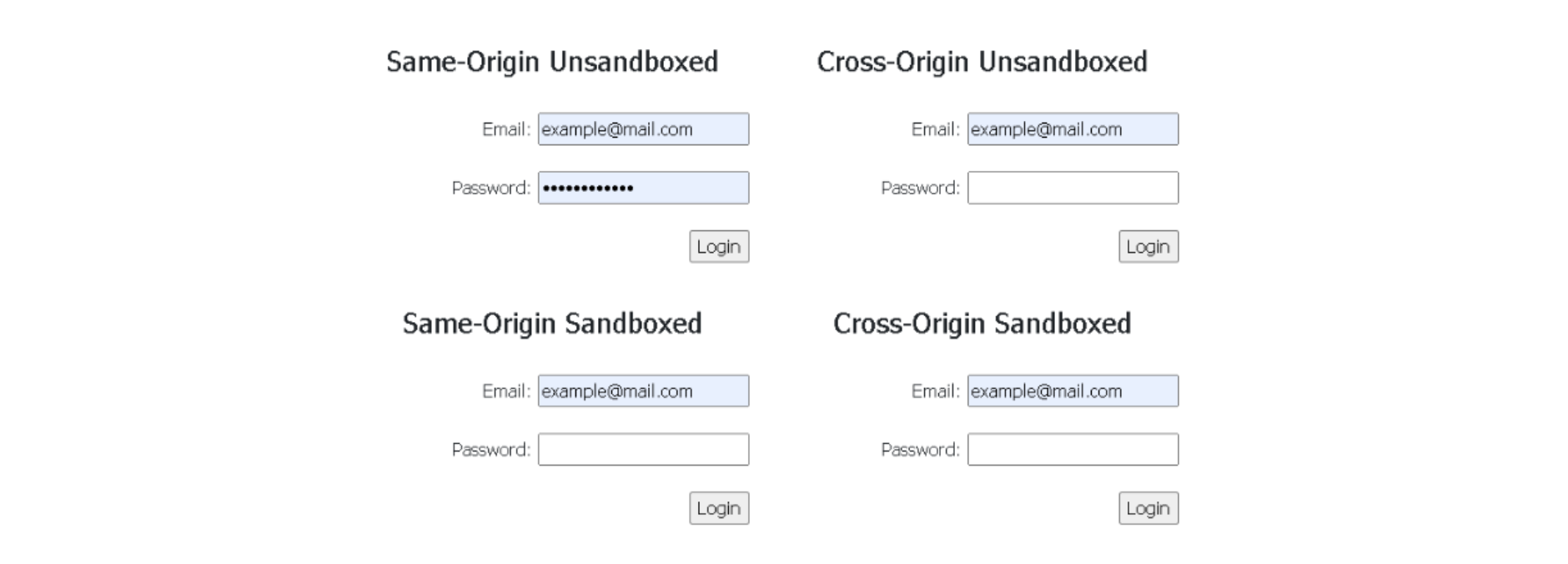 Image 3: Edge browser auto-fills username/email fields in all iframes
Image 3: Edge browser auto-fills username/email fields in all iframes
4. Bitwarden
BitWarden shows a warning prompt to the user, informing him that the credentials are about to be sent to a domain that is different from the current one.
This prompt lets the user decide whether he actually wants that form auto-filled or not, and if he accepts, the extension will auto-fill unsandboxed cross-origin iframes.
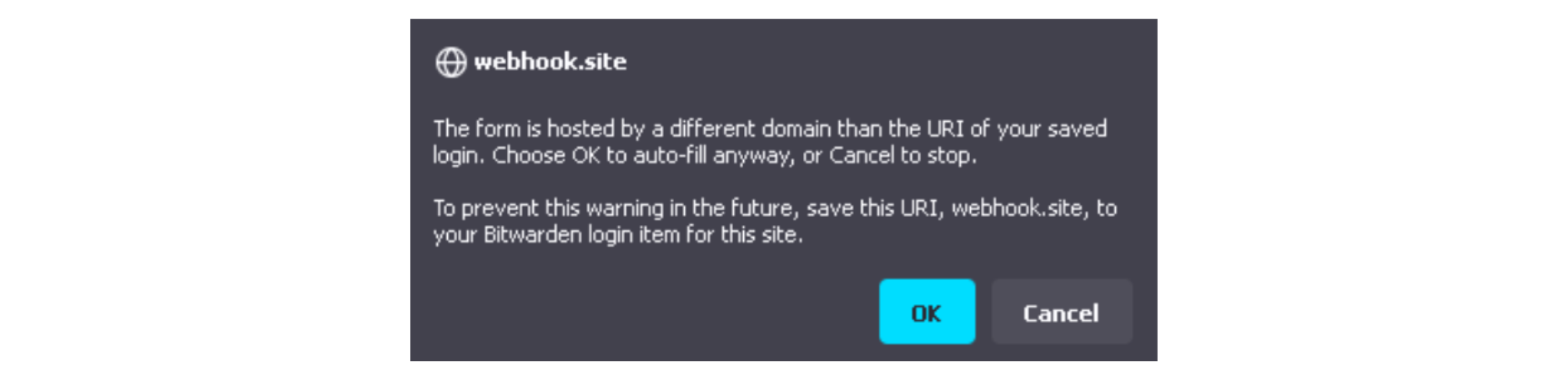 Image 4: Bitwarden extension warning the user about auto-filling cross-origin iframes
Image 4: Bitwarden extension warning the user about auto-filling cross-origin iframes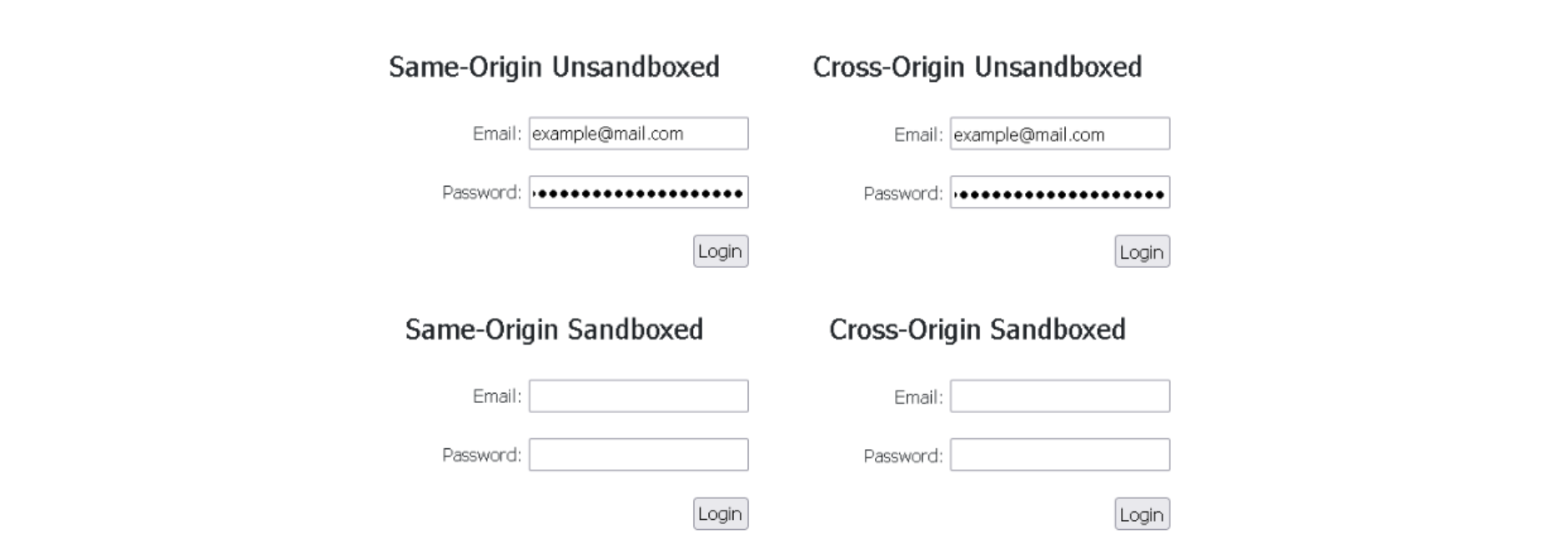 Image 5: Bitwarden extension filling same-origin and cross-origin iframes, if the user consents
Image 5: Bitwarden extension filling same-origin and cross-origin iframes, if the user consents
5. LastPass
Like BitWarden, LastPass will also show a warning prompt to the user, informing that the credentials are about to be sent to a domain that is different from the current one. If he accepts, the extension will also auto-fill unsandboxed cross-origin iframes.
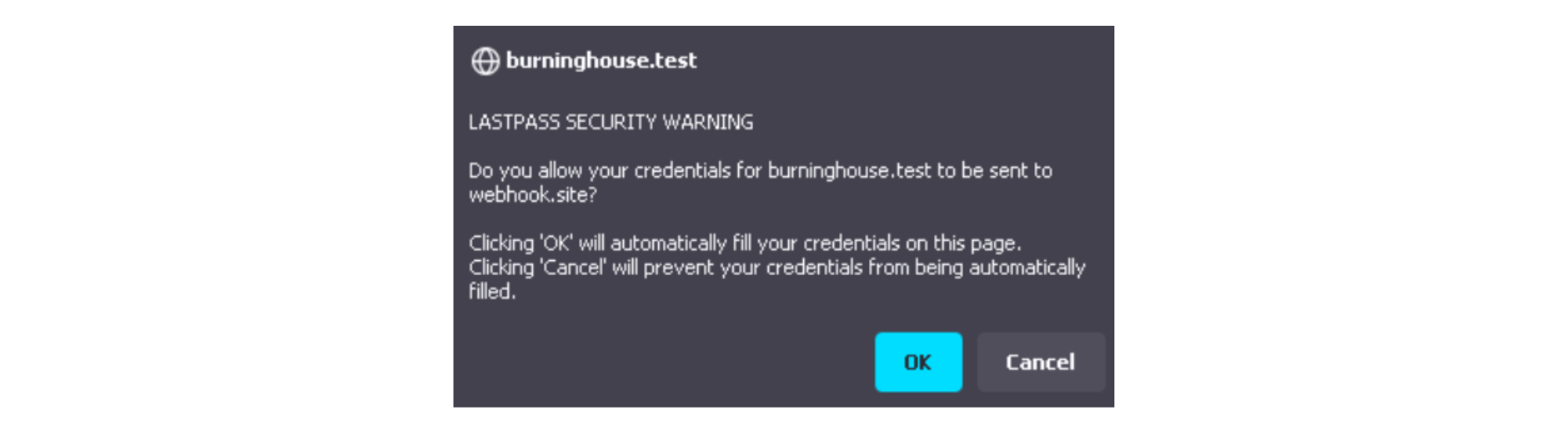 Image 6: LastPass extension warning the user about auto-filling cross-origin iframes
Image 6: LastPass extension warning the user about auto-filling cross-origin iframes
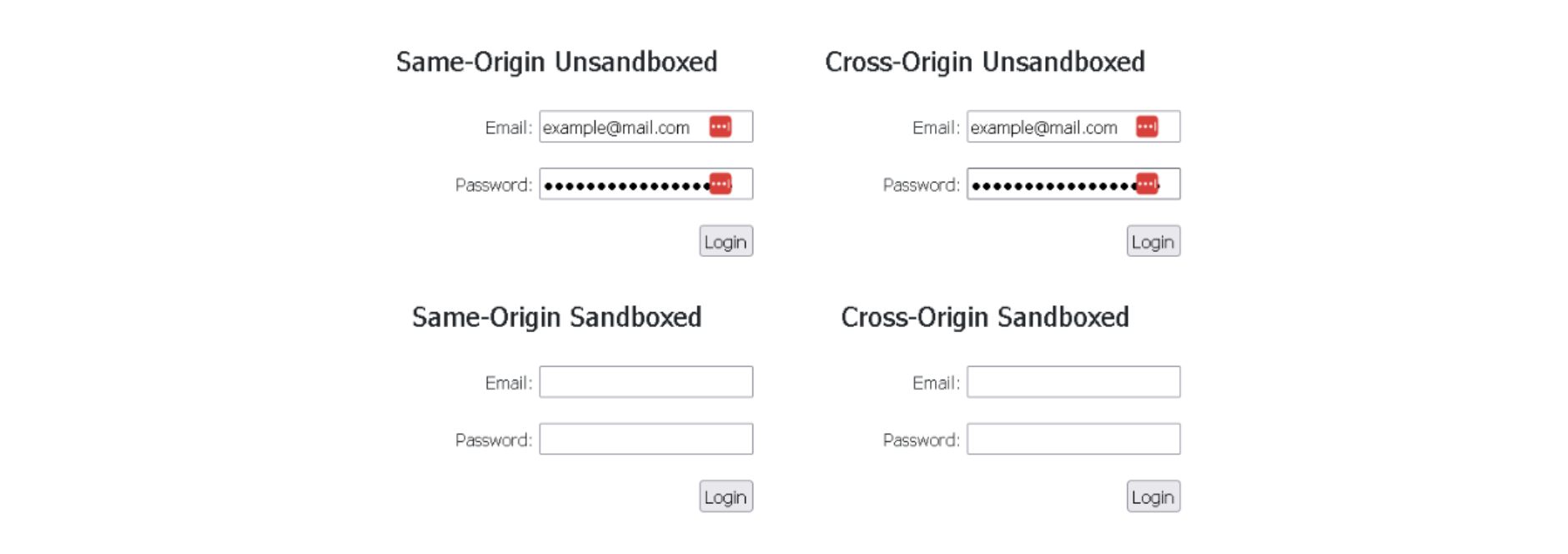 Image 7: LastPass extension filling same-origin and cross-origin iframes, if the user consents
Image 7: LastPass extension filling same-origin and cross-origin iframes, if the user consents
6. Passbolt
From the password managers that were tested, Passbolt was found to be one of the most secure, as it does not auto-fill or even present the auto-fill option to the user, in cross-origin or sandboxed iframes.
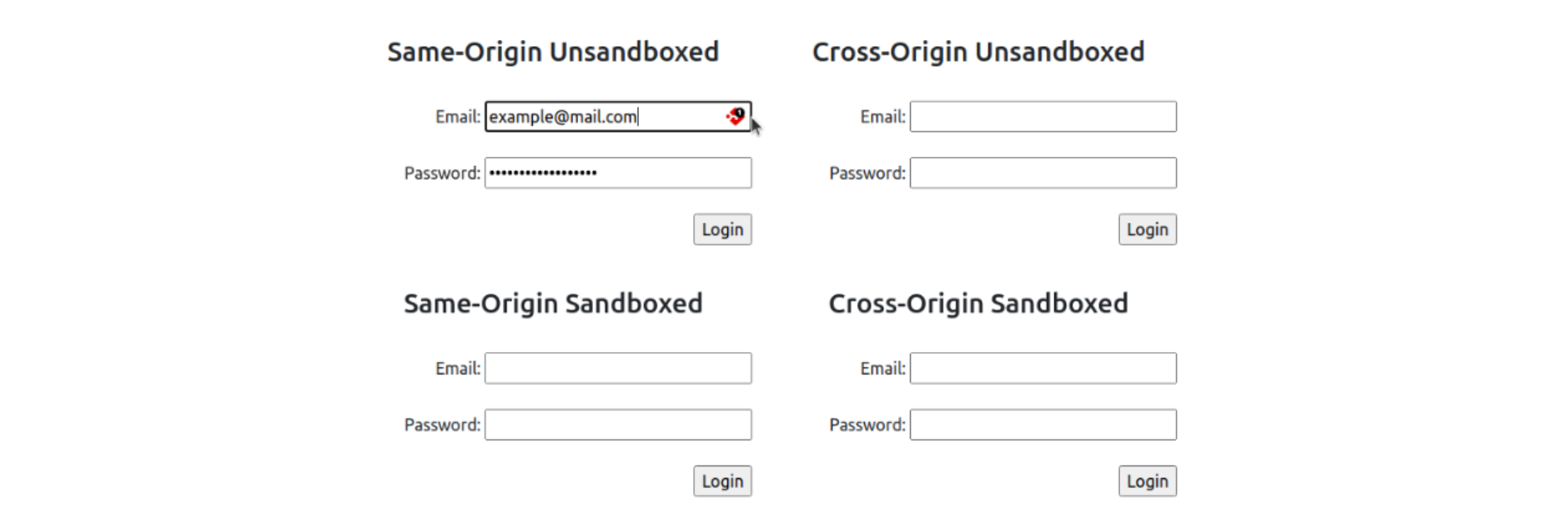 Image 8: Passbolt extension only auto-fills the same-origin unsandboxed iframe
Image 8: Passbolt extension only auto-fills the same-origin unsandboxed iframe
7. 1Password
1Password did also display the behavior we were expecting. It does not auto-fill or even present the auto-fill option to the user in cross-origin or sandboxed iframes, just like Passbolt.
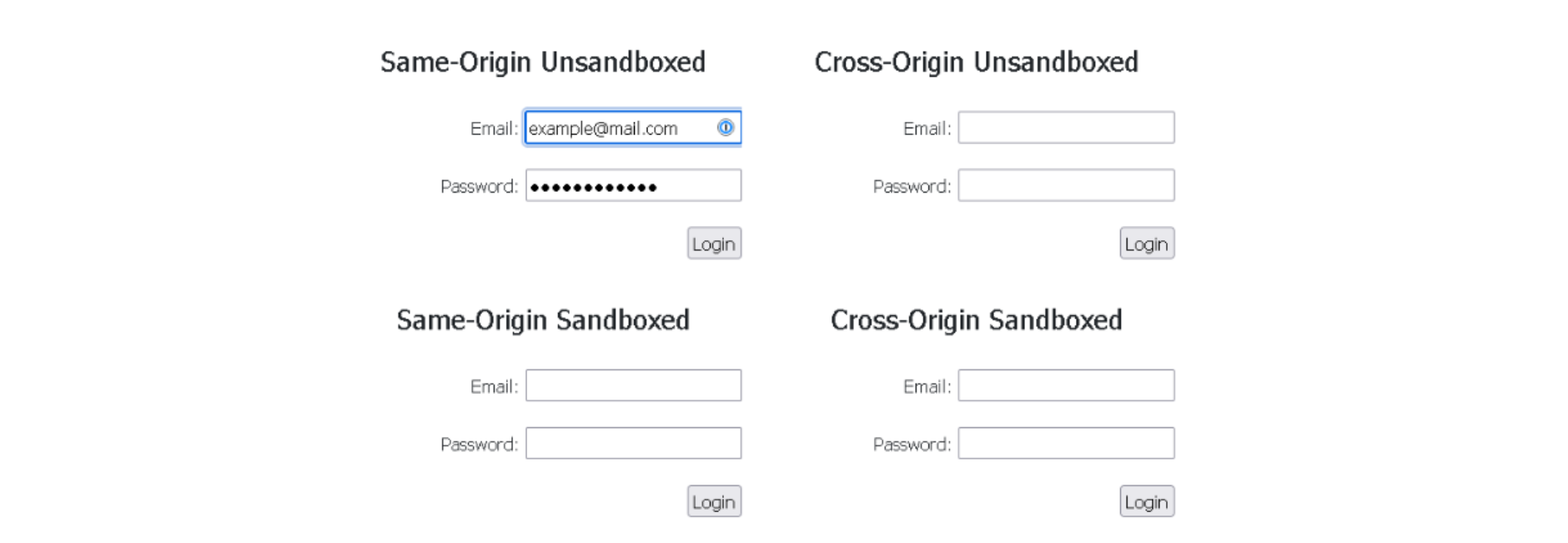 Image 9: 1Password extension only auto-fills the same-origin unsandboxed iframe
Image 9: 1Password extension only auto-fills the same-origin unsandboxed iframe
Conclusion
While password managers are powerful tools for enhancing online security, users must remain vigilant and understand the potential risks associated with auto-fill functionality.
We suggest that users disable the automatic auto-fill feature on their password managers and instead choose to trigger the auto-fill manually only when they are confident that the form presented is legitimate and should be filled.
Remember, the key to secure password management lies not only in the technology but also in the user's responsible and proactive approach to online security.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
How to Store Passwords Safely
Security of users' passwords is one of the most important aspect of developing your web application.
September 22, 2016 | By Jscrambler | 11 min read
Closing Security Gaps in Mobile Apps With Source Code Protection
As mobile apps across the globe keep being breached, closing security gaps and protecting the source code is key to fend attackers off and reduce the attack surface.
September 29, 2020 | By Pedro Fortuna | 3 min read
